On June 28, 2016, a team of three suicide operatives arrived in a taxi at Istanbul’s Ataturk international airport dressed in heavy jackets concealing suicide vests and carrying bags with AK-47 assault rifles. The first attacker detonated his bomb on the second floor of the international departure hall. The other two attackers approached the x-ray security checkpoint inside the international terminal and opened fire against travelers and subsequently detonating their vests. The coordinated attack killed more than 40 people and wounded more than 230 in 90 seconds.
On November 13, 2015, eight terrorist operatives divided into three teams and equipped with assault rifles and suicide vests, simultaneously attacked six locations across Paris, France. The gunmen arrived by car at the various targets that included restaurants, bars, a concert venue, and a sports arena. A hostage standoff lasting nearly three hours unfolded at the Bataclan concert hall. In less than three hours, the three teams killed 130 and injured several hundred across Paris.
These attacks are two of several against soft targets in the past year, including hotels, nightclubs, airport terminals, and sporting events across the globe. The attacks are difficult to comprehend and easy to dismiss as senseless acts without any logic behind them. So, what is the underlying thought process behind attacking soft targets? And what measures can the private sector implement to detect and prevent future mass casualty attacks?
Soft Targets – Operational characteristics that are easy to exploit
Attacks against soft targets are attractive because soft targets have operational characteristics that make them vulnerable and easy to exploit, thereby ensuring higher success. To accomplish this objective, the layout of these venues must fulfill certain criteria, including an inviting atmosphere for visitors that is usually open and spacious.
Many soft targets such as shopping malls, movie theaters, hotels, and airport terminals have multiple entrances and exits and allow direct access from streets or subway stations. They also offer the ability to unload passengers and luggage close to the site perimeter. Soft targets also offer parking lots located in very close proximity to venue sites to accommodate families and the disabled.
Additionally, these sites frequently lack visible security guards and detailed screenings prior to entry to prevent deterring and scaring away visitors. Many security guards at soft targets also lack the training and proper equipment to respond to a terrorist attack.
Moreover, the lack of proper screening of individuals and cars allows actors to enter premises with weapons and explosives and park vehicle borne explosive devices in close proximity to malls, restaurants, hotels, and movie theaters.
Selection of soft targets is driven by strategic objectives
The first stage in the terrorist attack cycle, commonly referred to as the target selection process, is often driven by strategic and ideological objectives. Targets are also selected in response to what security measures exist in the operational environment.
Terrorists can be viewed as rational actors in the sense that they engage in a calculation of costs and benefits when selecting a target. If a high profile and symbolic target such as a foreign embassy or high-level meeting are hardened, a threat actor with limited capabilities can substitute the hardened target with a softer target that guarantees a higher level of success.
Primarily then, terrorists choose soft targets because they are easy to attack and do not require a long planning cycle. Soft targets are ideal for terrorist groups that are under pressure and seek quick retaliatory attacks eager to demonstrate their resolve and resiliency for enemies and supporters alike. ISIS retributive attacks against soft targets among U.S. coalition partners could be viewed as an attempt to demonstrate ISIS’ continued relevance amid territorial losses.
Attacks against soft targets with high civilian losses can generate global media attention that magnifies the terrorist groups’ cause, satisfies their supporters, and attracts new recruits.
From a terrorist perspective, attacks against hotels, shopping malls, and restaurants can maximize media attention. In particular, attackers take hostages that prolong the drama and result in live media coverage rather than after the fact coverage.
Terrorist groups also attack soft targets for other strategic reasons too. Attacks can aim to dissuade foreign investments and undermine industry sectors of an economy in an effort to weaken the adversary. For example, the Turkish tourism sector is currently under pressure and heading towards a 35-40 percent drop in revenues during 2016 due to continuous attacks by the Kurdistan Worker’s Party and ISIS.
Lastly, attacks against soft targets causing mass causalities are also motivated by ideology and worldview. Threat actors that subscribe to religious or apocalyptic causes are generally predisposed to attack targets with a high concentration of civilians.
Such actors view the world as a dichotomy between good and evil. They have absolutist or non-negotiable goals and often seek to purify a corrupt religion, expel foreigners, eradicate societal structures, or hasten the end of the world. Moral codes are absent and enemies are de-humanized, which eliminate any moral barriers towards committing mass killing of civilians, including women and children.
Measures to detect and prevent pre-operational surveillance and attacks on soft targets
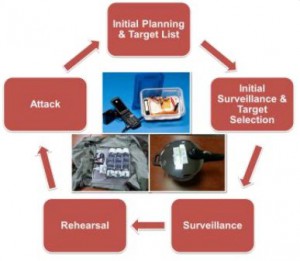
The private sector can detect and prevent future attacks by paying close attention to the pre-operational or surveillance/reconnaissance aspect of the attack cycle. The surveillance/reconnaissance stage is conducted to gain a profile of the target, determine the most suitable attack approach, and determine the best time to attack.
Threat actors may visit their intended target several times before initiating an attack. Therefore, employees and private actors can play an important role by being observant to detect any suspicious behavior that could indicate an upcoming attack. This includes:
- Being cognizant of any unusual interest or questions about security procedures, including access controls, delivery gates, security badges, alarms, doors, gates, cameras, locks, and security reaction drills. Threat actors can conduct surveillance by using a variety of equipment, cameras, binoculars, zoom lenses, and global positioning systems (GPS).
- Being aware of unusual incidents such as multiple fire alarms or fictitious emergency calls to the same location. Such actions could indicate a test of security to gather information on security responses, behavior, and response times.
- Being conscious of any car parked in the same area or location over multiple days and efforts to avoid surveillance cameras. Prolonged static surveillance can indicate hostile reconnaissance.
- Being alert to an unusual interest in egress and ingress points, peak days, hours of operation, site plans, security guards, and other employees.
- Increasing security awareness among staff (security guards, cleaning staff, maintenance and contractors) and encouraging suspicious activity reporting.
- Private venues with security guards can perform active and unpredictable patrolling in internal and external areas, particularly before and during special events and holidays.
- Conducting pre-employment screening of new personnel and existing staff to identify any derogatory information.
- Installing and utilizing CCTC systems to help identify planning activity.
globalriskinsights.com/